Wiresharkのインストール
Wiresharkをダウンロードする。
https://www.wireshark.org/#download
インストール時、「Install Npcap」にチェックが入っているので、チェックが入ったまま「Next」をクリックして進める。
「Install USBPcap」については、チェックが入っていないので、チェックが入っていない状態で「Next」をクリックして進める。これは、USB通信のキャプチャーを行う際に使用するが、今回は使用しない。
ハンドシェイクの流れ
Client:アクセスするパソコンやスマートフォン等に相当
Server:ウェブサーバー
Client(パソコン、スマートフォン等) Server(ウェブサーバー)
ClientHello -------->
クライアントが最初にサーバーに接続
使用可能な暗号スイートをすべて提示
ServerHello
サーバーが暗号スイートを1つに決定
Certificate*
TLSサーバー証明書
ServerKeyExchange*
鍵交換パラメーター
CertificateRequest*
クライアント認証利用時は証明書要求
<-------- ServerHelloDone
サーバーからの送信完了
Certificate*
クライアント認証時はクライアント認証証明書
ClientKeyExchange
鍵交換パラメーター
CertificateVerify*
クライアント認証証明書の検証
[ChangeCipherSpec]
この後に続くデータは保護されていると通知
Finished -------->
鍵交換と認証処理が成功したことを確認
[ChangeCipherSpec]
この後に続くデータは保護されていると通知
<-------- Finished
鍵交換と認証処理が成功したことを確認
Application Data <-------> Application Data
保護された通信のやりとり 保護された通信のやりとり
Fig. 1 - Message flow for a full handshake
* 常に送信されないオプション参照:
Request for Comments: 5246 The Transport Layer Security (TLS) Protocol Version 1.2
7.3. Handshake Protocol overview
Fig. 1 – Message flow for a full handshake
Request for Comments: 2246 The TLS Protocol Version 1.0
7.3. Handshake Protocol overview
Fig. 1 – Message flow for a full handshake
Wiresharkで確認
「tcp」に条件を絞り込み表示させた。
https://toyokeizai.net/にアクセスして、テストを実施した。
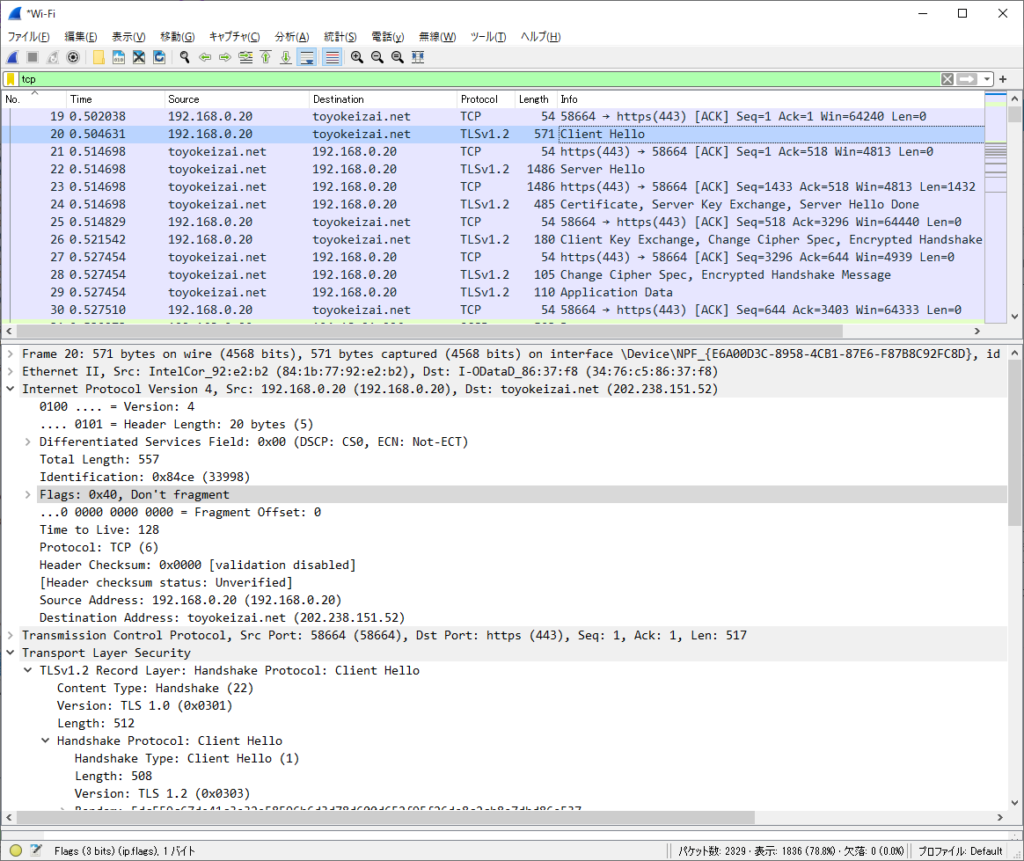
ClientHello (Client => Server)
クライアントが最初にサーバーに接続する。
使用可能な暗号スイートをすべて提示する。
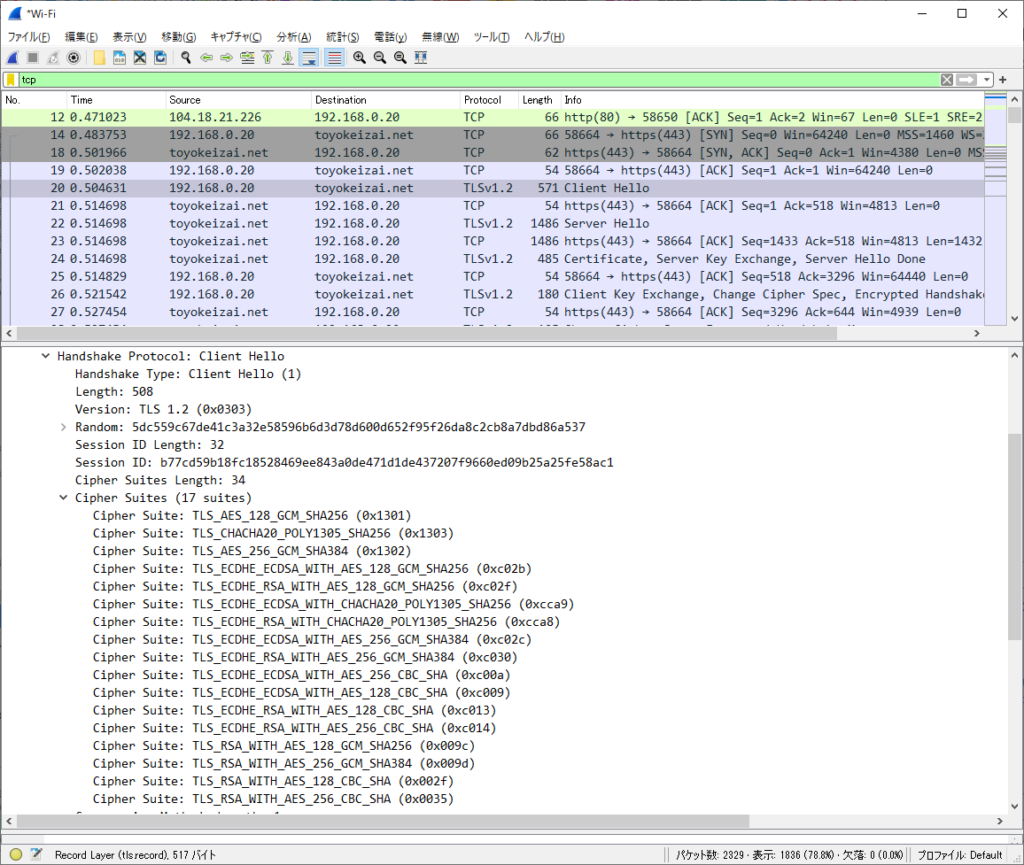
「Cipher Suites」の中身を表示。
Frame 20: 571 bytes on wire (4568 bits), 571 bytes captured (4568 bits) on interface \Device\NPF_{E6A00D3C-8958-4CB1-87E6-F87B8C92FC8D}, id 0
Ethernet II, Src: IntelCor_92:e2:b2 (84:1b:77:92:e2:b2), Dst: I-ODataD_86:37:f8 (34:76:c5:86:37:f8)
Internet Protocol Version 4, Src: 192.168.0.20 (192.168.0.20), Dst: toyokeizai.net (202.238.151.52)
Transmission Control Protocol, Src Port: 58664 (58664), Dst Port: https (443), Seq: 1, Ack: 1, Len: 517
Transport Layer Security
TLSv1.2 Record Layer: Handshake Protocol: Client Hello
Content Type: Handshake (22)
Version: TLS 1.0 (0x0301)
Length: 512
Handshake Protocol: Client Hello
Handshake Type: Client Hello (1)
Length: 508
Version: TLS 1.2 (0x0303)
Random: 5dc559c67de41c3a32e58596b6d3d78d600d652f95f26da8c2cb8a7dbd86a537
Session ID Length: 32
Session ID: b77cd59b18fc18528469ee843a0de471d1de437207f9660ed09b25a25fe58ac1
Cipher Suites Length: 34
Cipher Suites (17 suites)
Cipher Suite: TLS_AES_128_GCM_SHA256 (0x1301)
Cipher Suite: TLS_CHACHA20_POLY1305_SHA256 (0x1303)
Cipher Suite: TLS_AES_256_GCM_SHA384 (0x1302)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (0xcca9)
Cipher Suite: TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (0xcca8)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xc02c)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (0xc00a)
Cipher Suite: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (0xc009)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013)
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014)
Cipher Suite: TLS_RSA_WITH_AES_128_GCM_SHA256 (0x009c)
Cipher Suite: TLS_RSA_WITH_AES_256_GCM_SHA384 (0x009d)
Cipher Suite: TLS_RSA_WITH_AES_128_CBC_SHA (0x002f)
Cipher Suite: TLS_RSA_WITH_AES_256_CBC_SHA (0x0035)
Compression Methods Length: 1
Compression Methods (1 method)
Extensions Length: 401
Extension: server_name (len=19)
Extension: extended_master_secret (len=0)
Extension: renegotiation_info (len=1)
Extension: supported_groups (len=14)
Extension: ec_point_formats (len=2)
Extension: session_ticket (len=0)
Extension: application_layer_protocol_negotiation (len=14)
Extension: status_request (len=5)
Extension: delegated_credentials (len=10)
Extension: key_share (len=107)
Extension: supported_versions (len=5)
Extension: signature_algorithms (len=24)
Extension: psk_key_exchange_modes (len=2)
Extension: record_size_limit (len=2)
Extension: padding (len=136)
[JA3 Fullstring: 771,4865-4867-4866-49195-49199-52393-52392-49196-49200-49162-49161-49171-49172-156-157-47-53,0-23-65281-10-11-35-16-5-34-51-43-13-45-28-21,29-23-24-25-256-257,0]
[JA3: 579ccef312d18482fc42e2b822ca2430]
ServerHello (Server => Client)
Serverが「Cipher Suites」を1つに決定する。
今回は、以下に決定された。
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f)
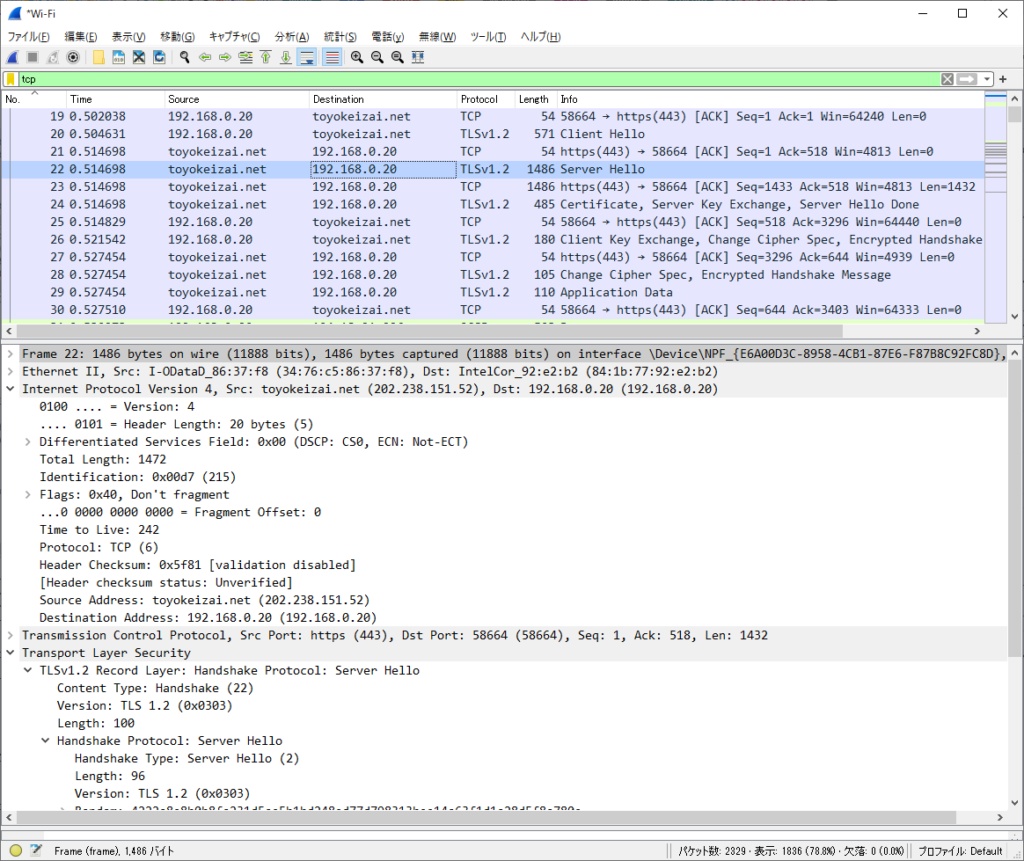
Frame 22: 1486 bytes on wire (11888 bits), 1486 bytes captured (11888 bits) on interface \Device\NPF_{E6A00D3C-8958-4CB1-87E6-F87B8C92FC8D}, id 0
Ethernet II, Src: I-ODataD_86:37:f8 (34:76:c5:86:37:f8), Dst: IntelCor_92:e2:b2 (84:1b:77:92:e2:b2)
Internet Protocol Version 4, Src: toyokeizai.net (202.238.151.52), Dst: 192.168.0.20 (192.168.0.20)
Transmission Control Protocol, Src Port: https (443), Dst Port: 58664 (58664), Seq: 1, Ack: 518, Len: 1432
Transport Layer Security
TLSv1.2 Record Layer: Handshake Protocol: Server Hello
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Length: 100
Handshake Protocol: Server Hello
Handshake Type: Server Hello (2)
Length: 96
Version: TLS 1.2 (0x0303)
Random: 4222a8e8b0b8fa231d5ae5b1bd248ed77d798313bee14a63f1d1a28d5f8a780e
Session ID Length: 32
Session ID: 528854a2a6cdc8863a504cb60d15700c94ab326a58ae103885f700d9dea5c01f
Cipher Suite: TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f)
Compression Method: null (0)
Extensions Length: 24
Extension: renegotiation_info (len=1)
Extension: application_layer_protocol_negotiation (len=5)
Extension: ec_point_formats (len=2)
Extension: extended_master_secret (len=0)
[JA3S Fullstring: 771,49199,65281-16-11-23]
[JA3S: c1108ede158e8e91e75c07b453533fb8]Certificate, ServerKeyExchange, ServerHelloDone (Server => Client)
Certificate:TLSサーバー証明書。
ServerKeyExchange:鍵交換パラメーター。
ServerHelloDone:サーバーからの送信完了。
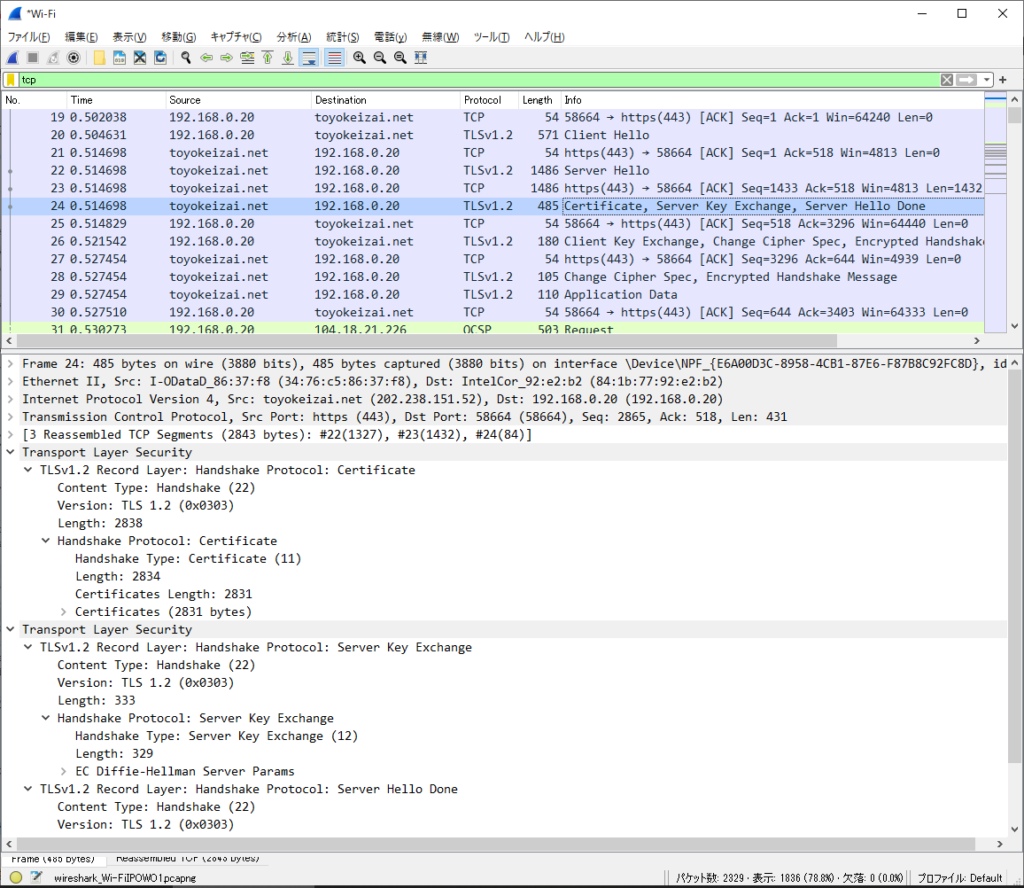
Frame 24: 485 bytes on wire (3880 bits), 485 bytes captured (3880 bits) on interface \Device\NPF_{E6A00D3C-8958-4CB1-87E6-F87B8C92FC8D}, id 0
Ethernet II, Src: I-ODataD_86:37:f8 (34:76:c5:86:37:f8), Dst: IntelCor_92:e2:b2 (84:1b:77:92:e2:b2)
Internet Protocol Version 4, Src: toyokeizai.net (202.238.151.52), Dst: 192.168.0.20 (192.168.0.20)
Transmission Control Protocol, Src Port: https (443), Dst Port: 58664 (58664), Seq: 2865, Ack: 518, Len: 431
[3 Reassembled TCP Segments (2843 bytes): #22(1327), #23(1432), #24(84)]
Transport Layer Security
TLSv1.2 Record Layer: Handshake Protocol: Certificate
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Length: 2838
Handshake Protocol: Certificate
Handshake Type: Certificate (11)
Length: 2834
Certificates Length: 2831
Certificates (2831 bytes)
Certificate Length: 1719
Certificate: 308206b33082059ba003020102020c3840e37bf79ed884cf3ef41d300d06092a864886f7… (id-at-commonName=.toyokeizai.net,id-at-organizationName=TOYO KEIZAI INC.,id-at-organizationalUnitName=Digital Media Bureau,id-at-localityName=CHUO-K signedCertificate version: v3 (2) serialNumber: 0x3840e37bf79ed884cf3ef41d signature (sha256WithRSAEncryption) issuer: rdnSequence (0) rdnSequence: 3 items (id-at-commonName=GlobalSign RSA OV SSL CA 2018,id-at-organizationName=GlobalSign nv-sa,id-at-countryName=BE) RDNSequence item: 1 item (id-at-countryName=BE) RDNSequence item: 1 item (id-at-organizationName=GlobalSign nv-sa) RDNSequence item: 1 item (id-at-commonName=GlobalSign RSA OV SSL CA 2018) validity subject: rdnSequence (0) rdnSequence: 6 items (id-at-commonName=.toyokeizai.net,id-at-organizationName=TOYO KEIZAI INC.,id-at-organizationalUnitName=Digital Media Bureau,id-at-localityName=CHUO-KU,id-at-stateOrProvinceName=TOKYO,id-at-countryName=JP)
RDNSequence item: 1 item (id-at-countryName=JP)
RDNSequence item: 1 item (id-at-stateOrProvinceName=TOKYO)
RDNSequence item: 1 item (id-at-localityName=CHUO-KU)
RDNSequence item: 1 item (id-at-organizationalUnitName=Digital Media Bureau)
RDNSequence item: 1 item (id-at-organizationName=TOYO KEIZAI INC.)
RDNSequence item: 1 item (id-at-commonName=*.toyokeizai.net)
subjectPublicKeyInfo
extensions: 10 items
algorithmIdentifier (sha256WithRSAEncryption)
Padding: 0
encrypted: 0d84fc946b19c8307fc17fd077052be53c56f259e122505d1758279d41823b6e22299cbe…
Certificate Length: 1106
Certificate: 3082044e30820336a003020102020d01ee5f221dfc623bd4333a8557300d06092a864886… (id-at-commonName=GlobalSign RSA OV SSL CA 2018,id-at-organizationName=GlobalSign nv-sa,id-at-countryName=BE)
signedCertificate
version: v3 (2)
serialNumber: 0x01ee5f221dfc623bd4333a8557
signature (sha256WithRSAEncryption)
issuer: rdnSequence (0)
rdnSequence: 3 items (id-at-commonName=GlobalSign,id-at-organizationName=GlobalSign,id-at-organizationalUnitName=GlobalSign Root CA - R3)
RDNSequence item: 1 item (id-at-organizationalUnitName=GlobalSign Root CA - R3)
RDNSequence item: 1 item (id-at-organizationName=GlobalSign)
RDNSequence item: 1 item (id-at-commonName=GlobalSign)
validity
subject: rdnSequence (0)
rdnSequence: 3 items (id-at-commonName=GlobalSign RSA OV SSL CA 2018,id-at-organizationName=GlobalSign nv-sa,id-at-countryName=BE)
RDNSequence item: 1 item (id-at-countryName=BE)
RDNSequence item: 1 item (id-at-organizationName=GlobalSign nv-sa)
RDNSequence item: 1 item (id-at-commonName=GlobalSign RSA OV SSL CA 2018)
subjectPublicKeyInfo
extensions: 7 items
algorithmIdentifier (sha256WithRSAEncryption)
Padding: 0
encrypted: 9990c82d5f428ad40b66db98037311d488865228538afbaddffd738e3a6704dbc3531470…
Transport Layer Security
TLSv1.2 Record Layer: Handshake Protocol: Server Key Exchange
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Length: 333
Handshake Protocol: Server Key Exchange
Handshake Type: Server Key Exchange (12)
Length: 329
EC Diffie-Hellman Server Params
Curve Type: named_curve (0x03)
Named Curve: secp256r1 (0x0017)
Pubkey Length: 65
Pubkey: 04aaba6517c0b2ff6876a925e90e80d94209591e845e702c670171d17eeb939a07b37824…
Signature Algorithm: rsa_pkcs1_sha256 (0x0401)
Signature Length: 256
Signature: 183ec0a001313f12a786355237a0fc7f5ea21901af88fa89ddb667dd5866fa15de9daa5c…
TLSv1.2 Record Layer: Handshake Protocol: Server Hello Done
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Length: 4
Handshake Protocol: Server Hello Done
Handshake Type: Server Hello Done (14)
Length: 0ClientKeyExchange, ChangeCipherSpec, Finished (Client => Server)
ClientKeyExchange:鍵交換パラメーター。
ChangeCipherSpec:この後に続くデータは保護されていると通知。
Finished:鍵交換と認証処理が成功したことを確認。「Encrypted Handshake Message」は同じ意味になる。
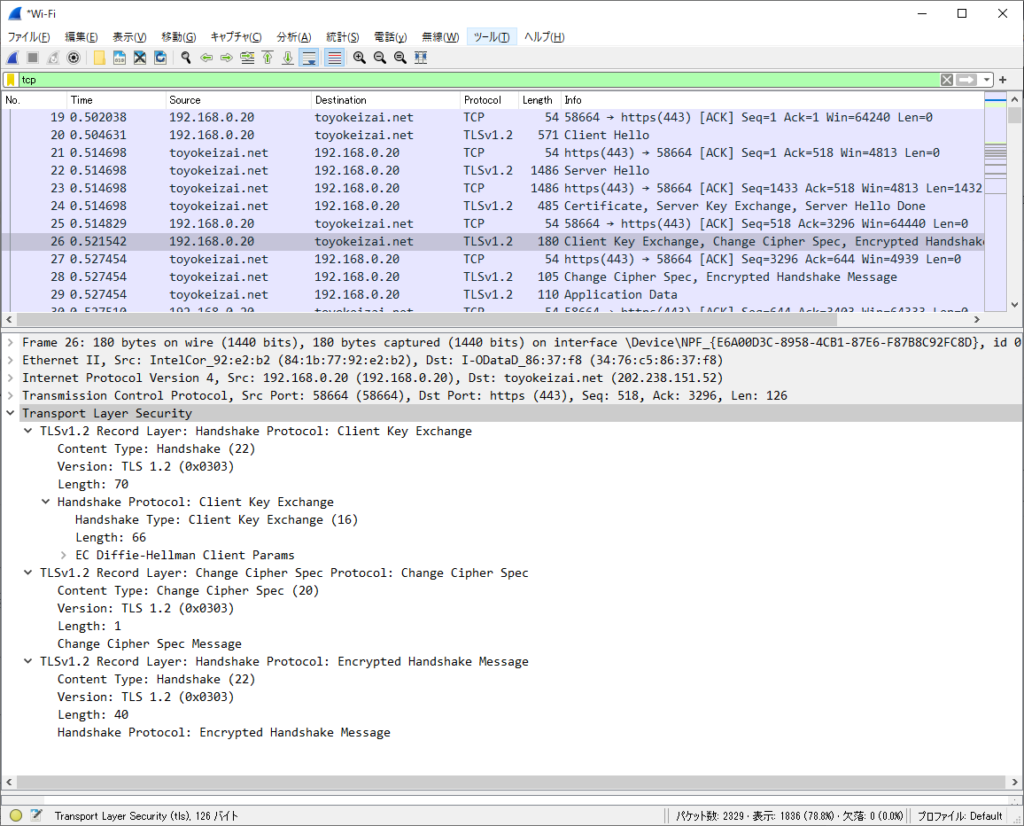
Frame 26: 180 bytes on wire (1440 bits), 180 bytes captured (1440 bits) on interface \Device\NPF_{E6A00D3C-8958-4CB1-87E6-F87B8C92FC8D}, id 0
Ethernet II, Src: IntelCor_92:e2:b2 (84:1b:77:92:e2:b2), Dst: I-ODataD_86:37:f8 (34:76:c5:86:37:f8)
Internet Protocol Version 4, Src: 192.168.0.20 (192.168.0.20), Dst: toyokeizai.net (202.238.151.52)
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 166
Identification: 0x84d0 (34000)
Flags: 0x40, Don't fragment
...0 0000 0000 0000 = Fragment Offset: 0
Time to Live: 128
Protocol: TCP (6)
Header Checksum: 0x0000 [validation disabled]
[Header checksum status: Unverified]
Source Address: 192.168.0.20 (192.168.0.20)
Destination Address: toyokeizai.net (202.238.151.52)
Transmission Control Protocol, Src Port: 58664 (58664), Dst Port: https (443), Seq: 518, Ack: 3296, Len: 126
Transport Layer Security
TLSv1.2 Record Layer: Handshake Protocol: Client Key Exchange
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Length: 70
Handshake Protocol: Client Key Exchange
Handshake Type: Client Key Exchange (16)
Length: 66
EC Diffie-Hellman Client Params
Pubkey Length: 65
Pubkey: 04b82572f15779978613561fa1615e8024a58fd8141e665d5d3ebe9f8c3d5e56e7b7f4f3…
TLSv1.2 Record Layer: Change Cipher Spec Protocol: Change Cipher Spec
Content Type: Change Cipher Spec (20)
Version: TLS 1.2 (0x0303)
Length: 1
Change Cipher Spec Message
TLSv1.2 Record Layer: Handshake Protocol: Encrypted Handshake Message
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Length: 40
Handshake Protocol: Encrypted Handshake MessageChangeCipherSpec, Finished (Server => Client)
ChangeCipherSpec:この後に続くデータは保護されていると通知。
Finished:鍵交換と認証処理が成功したことを確認。「Encrypted Handshake Message」は同じ意味になる。
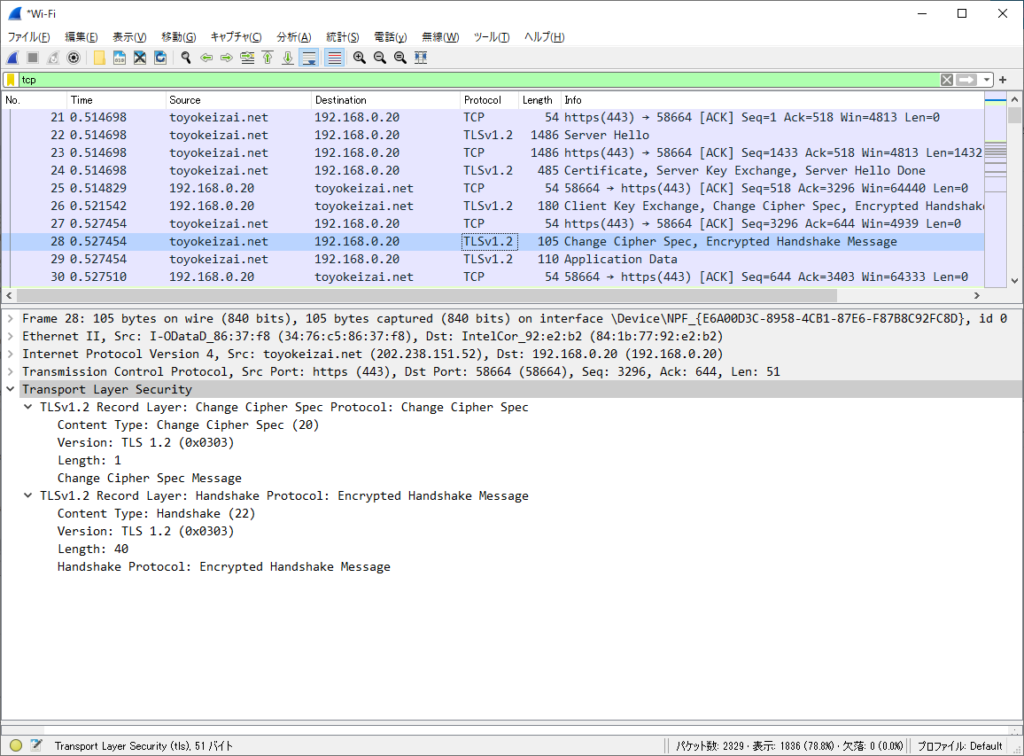
Frame 28: 105 bytes on wire (840 bits), 105 bytes captured (840 bits) on interface \Device\NPF_{E6A00D3C-8958-4CB1-87E6-F87B8C92FC8D}, id 0
Ethernet II, Src: I-ODataD_86:37:f8 (34:76:c5:86:37:f8), Dst: IntelCor_92:e2:b2 (84:1b:77:92:e2:b2)
Internet Protocol Version 4, Src: toyokeizai.net (202.238.151.52), Dst: 192.168.0.20 (192.168.0.20)
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 91
Identification: 0x02e6 (742)
Flags: 0x40, Don't fragment
...0 0000 0000 0000 = Fragment Offset: 0
Time to Live: 242
Protocol: TCP (6)
Header Checksum: 0x62d7 [validation disabled]
[Header checksum status: Unverified]
Source Address: toyokeizai.net (202.238.151.52)
Destination Address: 192.168.0.20 (192.168.0.20)
Transmission Control Protocol, Src Port: https (443), Dst Port: 58664 (58664), Seq: 3296, Ack: 644, Len: 51
Transport Layer Security
TLSv1.2 Record Layer: Change Cipher Spec Protocol: Change Cipher Spec
Content Type: Change Cipher Spec (20)
Version: TLS 1.2 (0x0303)
Length: 1
Change Cipher Spec Message
TLSv1.2 Record Layer: Handshake Protocol: Encrypted Handshake Message
Content Type: Handshake (22)
Version: TLS 1.2 (0x0303)
Length: 40
Handshake Protocol: Encrypted Handshake MessageApplication Data (Client <=> Server)
Application Data:保護された通信のやりとり
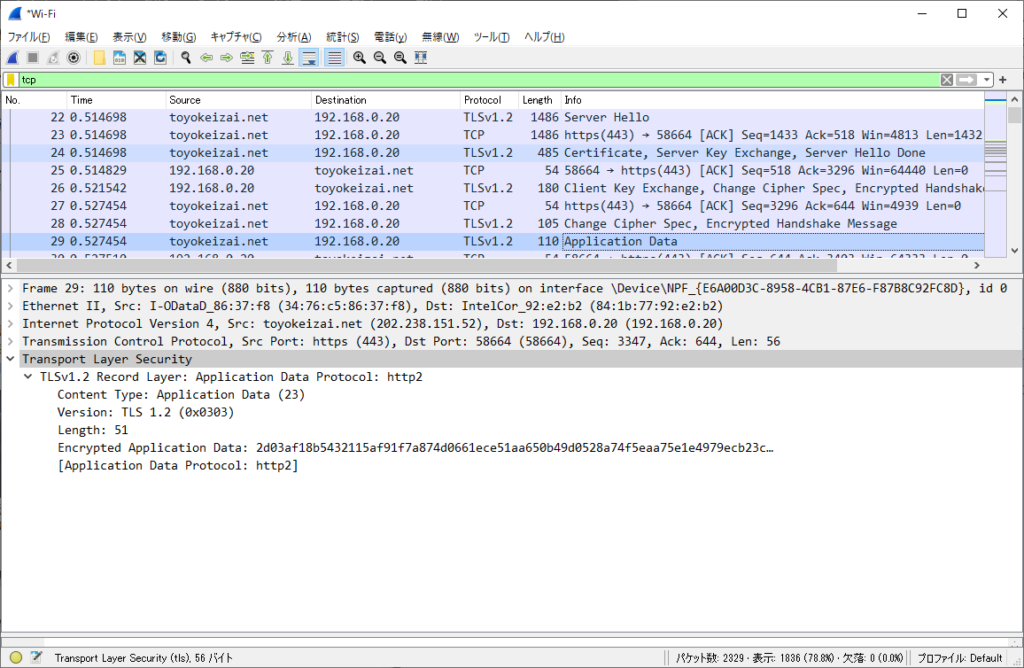
Frame 29: 110 bytes on wire (880 bits), 110 bytes captured (880 bits) on interface \Device\NPF_{E6A00D3C-8958-4CB1-87E6-F87B8C92FC8D}, id 0
Ethernet II, Src: I-ODataD_86:37:f8 (34:76:c5:86:37:f8), Dst: IntelCor_92:e2:b2 (84:1b:77:92:e2:b2)
Internet Protocol Version 4, Src: toyokeizai.net (202.238.151.52), Dst: 192.168.0.20 (192.168.0.20)
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 96
Identification: 0x02eb (747)
Flags: 0x40, Don't fragment
...0 0000 0000 0000 = Fragment Offset: 0
Time to Live: 242
Protocol: TCP (6)
Header Checksum: 0x62cd [validation disabled]
[Header checksum status: Unverified]
Source Address: toyokeizai.net (202.238.151.52)
Destination Address: 192.168.0.20 (192.168.0.20)
Transmission Control Protocol, Src Port: https (443), Dst Port: 58664 (58664), Seq: 3347, Ack: 644, Len: 56
Transport Layer Security
TLSv1.2 Record Layer: Application Data Protocol: http2
Content Type: Application Data (23)
Version: TLS 1.2 (0x0303)
Length: 51
Encrypted Application Data: 2d03af18b5432115af91f7a874d0661ece51aa650b49d0528a74f5eaa75e1e4979ecb23c…
[Application Data Protocol: http2]



